What is Ransomware? The reality of attacks and effective countermeasures
This page introduces the actual situation of ransomware attacks and effective countermeasures.
What is ransomware?
Ransomware is a word coined from “ransom” and “software.
It refers to malware (software) that uses a malicious program to encrypt documents, images, and other files on a terminal, or locks them so that they cannot be operated.
The malware infects the device with the virus and at the same time threatens to demand money in exchange for the encryption or unlocking of the files.
Once infected with the virus, it is difficult to recover data on one’s own, and the victim has no choice but to accept the ransom demand. For this reason, ransomware is also known as a ransom-demanding malware.
According to the “Information Security: 10 Major Threats to Information Security 2022” published annually by the Information-technology Promotion Agency (IPA), damage caused by ransomware is No. 1 among corporations.
This page explains the actual situation of ransomware attacks and effective countermeasures with HENNGE One’s functions.
Information Security 10 Major Threats 2023 Ranking of Threats to Individuals and Organizations
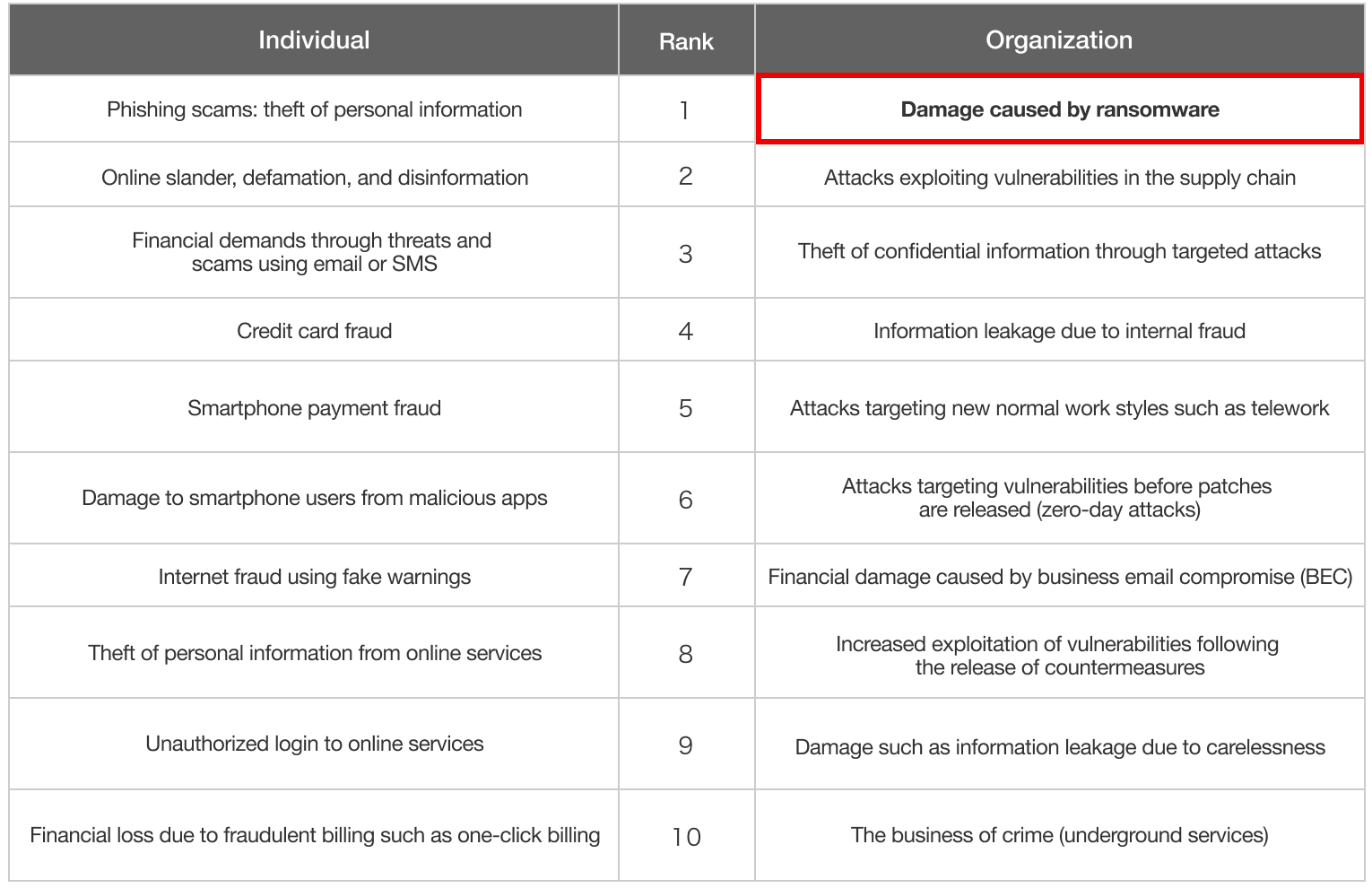
*From IPA Information Security 10 Major Threats 2023
Major Types of Ransomware
There are several types of ransomware, each using different methods to cause damage. The main types of ransomware are described below.
Crypto Ransomware
Crypto ransomware encrypts files and demands a ransom to decrypt them. The encrypted data cannot be restored by the user and cannot be recovered without the decryption key. WannaCry” and “Locky” are typical examples. This type often targets especially important corporate data.
Locker Ransomware
Locker ransomware locks the entire system and prevents users from accessing their computers. The files themselves are not encrypted, but the use of the system is restricted. Typically, a ransom message appears on the desktop, asking for payment to unlock the system.
Doxware (Leakware)
Doxware steals data, encrypts it, and threatens to expose it if the ransom is not paid. This type often targets personal information and company secrets, increasing the risk of data leakage. Victims consider paying to avoid loss of credibility due to exposed data.
The Reality of Ransomware Attacks – Impact and Damage
Ransomware tactics are becoming more sophisticated every day, and it is important to keep up-to-date with the latest countermeasures.
Phishing / Targeted Attack Emails
Emails disguised as a trusted sender or seemingly legitimate emails with a subject line and body such as a business contact or invoice are sent, but when the attachment or link is clicked, the email is infected with ransomware. Do not open suspicious e-mails easily, but carefully check the sender and contents.
Infection by Web sites
Ransomware is automatically downloaded by simply visiting a vulnerable website; keep your OS and software up-to-date and install security software to reduce the risk of infection.
Remote Desktop Protocol (RDP) attack
RDP vulnerabilities are exploited to allow ransomware to infiltrate your computer, so be sure to take thorough security measures such as not opening RDP ports, setting strong passwords, and implementing multi-factor authentication.
Supply Chain Attacks
Ransomware is planted in the software development and distribution process to infect numerous organizations and individuals. Be sure to obtain software from a trusted source and update it promptly.
Impact and Damage
Data loss
Ransomware encrypts critical files and systems, making them inaccessible. Without backups, data recovery will be difficult and may lead to business stoppages and information leaks.
Economic loss
In addition to the ransom payment, the company will be forced to bear a tremendous financial burden in terms of system restoration, security measure costs, and losses due to business stoppages. For small and medium-sized enterprises, this can be a blow that can put pressure on management.
Loss of trust
Ransomware damage can cause a loss of trust from customers and business partners. If personal information or trade secrets are leaked due to information leaks, social credibility may also be lost, making it difficult to continue business operations.
Ransomware Countermeasures
Among ransomware countermeasures, “network intrusion countermeasures” are particularly important. The Information Security White Paper explains that “a ransomware attack starts when an attacker infiltrates the network of a company or organization. Effective measures to prevent network intrusions include “countermeasures against attack e-mails (phishing e-mails/targeted attack e-mails),” “strengthening access control and authentication,” “minimizing attack surface areas (attack surfaces),” and “vulnerability countermeasures.
Countermeasure 01
Countermeasure 1 against attack e-mails
HENNGE Cloud Protection (phishing e-mails / targeted attack e-mails)
HENNGE Cloud Protection is an effective countermeasure against phishing/targeted email attacks, offering a variety of features to enhance email security. HENNGE Cloud Protection protects your organization from phishing emails through the following three key features.
Exchange items, including emails on Microsoft 365, are protected against threats.
1. Behavior Detection.
Behavior Detection identifies phishing emails by monitoring the behavior of attachments and other items in the email and detecting unusual behavior. Malicious emails often behave abnormally to trick recipients into entering sensitive information or downloading malware; HENNGE Cloud Protection detects these unusual behaviors and automatically blocks phishing emails. This greatly reduces the risk of users accidentally responding to phishing emails.
2. Reputation Checks.”
Reputation Check is a feature that evaluates the authenticity of an email’s source domain or IP address; HENNGE Cloud Protection filters emails from unreliable sources and blocks phishing emails in advance. This reduces the risk of phishing attacks by eliminating suspicious emails before recipients receive them. In addition, the use of a database that is updated in real time allows for rapid response to the latest threats.
3.The “Sandbox.”
The Sandbox feature detects malware and phishing attacks by running email attachments and links in a quarantined environment and analyzing their behavior; HENNGE Cloud Protection uses this feature to inspect emails in a secure environment to determine if they contain malicious content and to see if it contains any malicious content. This helps prevent threats before users click on dangerous links or open infected files.
Countermeasure 02
Attack Mail Countermeasure #2
HENNGE Tadrill (Targeted Attack Email Training)
HENNGE Tadrill, targeted attack email training, can lower the risk of ransomware attacks and other attacks through email, which is said to be difficult to prevent completely with antivirus alone, by improving employee literacy. It provides real-time feedback, responds to the latest attack methods, and improves the security level of the organization.
To learn more about HENNGE Tadrill, please visit the ” Tadrill for Targeted Attack Email Training Service ” page.
Countermeasure 03
Strengthening Access Control and Authentication
HENNGE Access Control
To prevent unauthorized access from outside, it is effective to limit the range of access using access control. HENNGE Access Control strengthens user authentication and prevents unauthorized access through multi-factor authentication (MFA) and single sign-on (SSO). Multi-factor authentication, in particular, requires additional authentication factors in addition to passwords, thus significantly increasing security. To learn more about HENNGE Access Control, please visit the On-Premise Secure Gate page.
Countermeasure 04
Attack Target Area (Attack Surface)
HENNGE Connect
Ransomware needs to be reduced from VPN devices, remote desktop services, and servers with Internet access, etc. HENNGE Connect is based on a zero-trust model and rigorously authenticates and verifies each access. This significantly reduces the risk of unauthorized access and ransomware entering the network. To learn more about HENNGE Connect, please visit our De-VPN Solutions page.
Countermeasure 05
Vulnerability Countermeasures
Ransomware attacks by exploiting vulnerabilities in devices and services. Therefore, it is recommended that both hardware and software be regularly upgraded and kept up-to-date.
In recent years, ransomware has become even more serious, with some cases of “double, triple, or quadruple threats” after the ransom demand for data has been successfully met. This is due to the fact that RaaS (Ransomware-as-a-Service) provides an environment where ransomware attacks can be easily carried out by anyone without specialized knowledge or advanced technology. However, most of the cyber-attacks, such as ransomware, use “exploiting misconfigurations or vulnerabilities in cloud services” as their intrusion routes and attack clues. In other words, the countermeasures we need to take are basically the same. Since there are several types of cyber-attack countermeasures, it is recommended that you first take drastic security measures that cover the basics, or implement a single solution that can implement multiple security measures.