2 Important Lessons Lapsus$ Taught Us
August 10, 2022
Who was Lapsus$
According to Wikipedia, Lapsus$ was a criminal hacker group which was first seen in December 2021. Until 7 members were arrested in March 2022, they managed to breach notable companies such as Nvidia, Microsoft, Samsung, Ubisoft, Okta and T-Mobile.
Basic operation is that they got into a corporate network using social engineering. After they acquire information, they threaten the company of disclosing that information.
Lesson1: Vulnerability is people
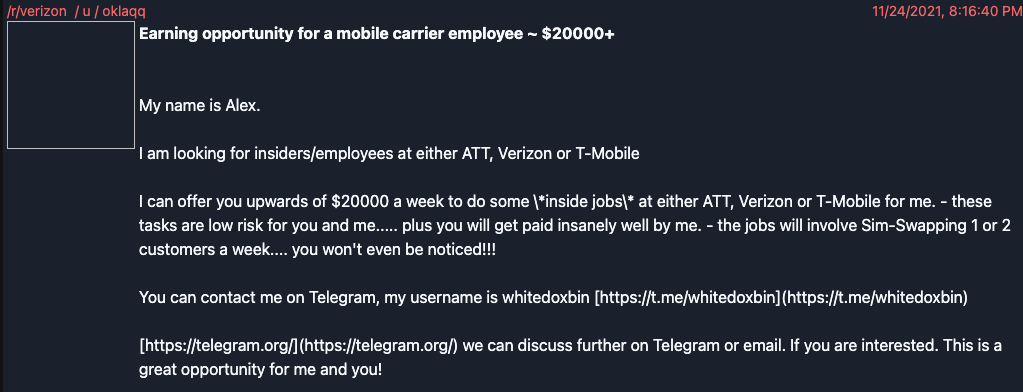
The key difference of Lapsus$ from other criminal hacker groups is that they heavily rely on social engineering. Many hacker groups attack system vulnerabilities to get into the system. And after setting the backdoor, they will acquire information. In fact, this requires good knowledge of IT and requires IT resources. This is the reason why there is Crime-as-a-Service (CaaS) which provides tools and resources for making cyber attacks. In contrast, Lapsus$ used social engineering which is to bribe people to get valid credentials to get into the system. The screenshot below from Reddit shows they offered $20,000 US dollar a week to do an “inside job”. It is easily imaginable that there are people attracted to that amount of money.
In some cases, Lapsus$ targeted contract workers to get into the system who are less related and less loyal to the company. Some contract workers may have more incentive on money and if those contract workers are not IT professionals, Lapsus$ might be able to persuade those people that what they are asking is no danger. In reality, giving identity to someone else can be traced so that the person providing identity will be at great risk but less IT education might make those kinds of people to be persuaded.
If the one accessing has valid credentials from a valid location, there is no way that the system can stop. And, there are always some people who are less loyal to the company especially if the company is using outside contract workers to reduce cost. The lesson we can learn from Lapsus$ is that people are always vulnerable and can be targeted by hackers any time. At this moment, members in Lapsus$ were mostly arrested. But, we need to be careful that there are always people who try to imitate.
Lesson2: Any information can damage
The news of a breach in the notable company is sensational. In fact, some of the information Lapsus$ acquired is just some conversations in the office which do not contain any critical information. However, since the act of breach itself already has great value, the value of information acquired doesn't mean anything.
This showed that evidential information of the fact which Lapsus$ managed to breach is just good enough to damage the credibility of the company. Of course the company will have a critical damage if a criminal hacker group obtains the highly confidential information. However, once the criminal hacker could get into the company network, no matter how less valuable the information they obtain is, the criminal hacker can damage the company.
This means keeping the company network private and shutting unauthorized or fake people out from the network is the most important matter.
Zero Trust is to “Trust But Verify”
“Trust But Verify” is the term which 40th president of the United States, Ronald Reagan used when he was negotiating with the Soviet Union on nuclear disarmament. This phrase is originally from Russian proverb “doveryay, no proveryay”. This term teaches us the importance of verification to trust anyone.
Zero trust is the methodology of “Never Trust, Always Verify” which also values the importance of verification. Our product HENNGE One is the solution which can provide a variety of ways to verify the person is trustworthy. And I believe that those security functions of HENNGE One to sign-in to cloud systems can help a company to pursue zero trust.
From 2 important lessons from Lapsus$, we learned the importance of verifying the people accessing the network even if the person has valid credentials. In order to do so, verifying users by using multiple methods is important.
喜歡這篇文章嗎?歡迎分享出去!